In cybersecurity, understanding an adversary’s identity, capabilities, and intent is critical to intelligent cyber defense. Attribution matters. Despite cyber threat intelligence tracking a multitude of

Executive Summary As organizations depend more on applications, devices and services to interact across hybrid environments, non-human identities are becoming more common. To enable secure

Skip ahead if you have heard this story, but when I started in anti-virus at Dr Solomon’s, Alan Solomon would share how he moved from

In today’s cyberthreat landscape, even seconds of delay can mean the difference between stopping a cyberattack or falling victim to ransomware. One major cause of

As with every Sophos Firewall release, v21.5 includes several quality-of-life enhancements that make day-to-day management easier. Watch this video for an overview of what’s new

For the latest discoveries in cyber research for the week of 9th June, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES American tax

Executive Summary Unit 42 researchers have identified a growing threat to cloud security: Linux Executable and Linkage Format (ELF) files that threat actors are developing

Executive Summary On 2024-05-26 Check Point published an article12 about the new CVE-2024-24919 classified as a high severity vulnerability that leads to an arbitrary file

The modern cyber battlefield doesn’t respect organisational boundaries. Across defence networks, critical structured, unstructured, and semi-structured data sits distributed and siloed in specialised environments —
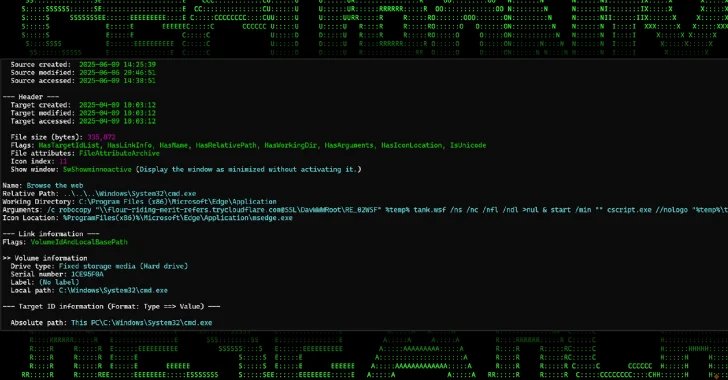
A new campaign is making use of Cloudflare Tunnel subdomains to host malicious payloads and deliver them via malicious attachments embedded in phishing emails. The
