Executive Summary This article outlines the mechanics and security implications of serverless authentication across major cloud platforms. Attackers target serverless functions in the hope of
Author: qku24
Executive Summary There has been a significant decrease in social engineering attacks linked to the Black Basta ransomware group since late December 2024. This lapse

In this blog you will hear directly from Microsoft’s Deputy Chief Information Security Officer (CISO) for Customer Security, Ann Johnson, about the need for proactive

Introduction 2024 was a whirlwind year—personally, professionally, and globally. We marveled at the spectacle of the Paris Summer Olympics, where the United States led the

Cybercriminals no longer need zero-day exploits or other vulnerabilities to breach your systems—these days, they just log in. On July 9th at 2:00 PM ET,

As the trend of remote work continues to gain momentum across the globe, companies are faced with a myriad of challenges, one of the most
In today’s interconnected world, businesses are no longer confined by geographical boundaries. The opportunity to tap into global talent pools is a game-changer, allowing companies

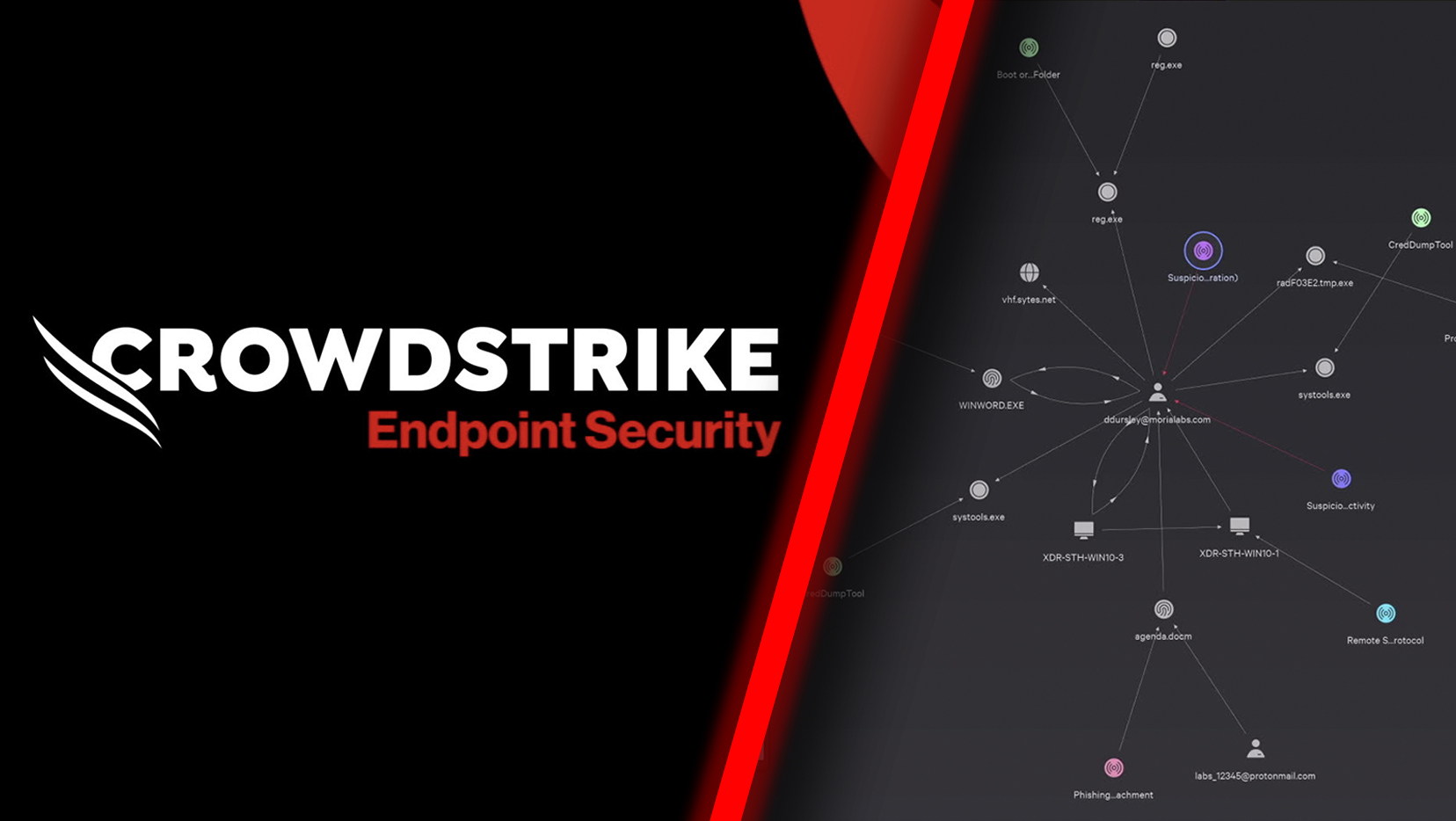
In today’s digital landscape, endpoint security has become a critical concern for organizations worldwide. With the increasing sophistication of cyber threats, businesses need robust solutions
In today’s digital landscape, the need for robust cybersecurity measures has never been more critical. As businesses increasingly migrate to cloud platforms for their scalability,
Ransomware attacks are one of the most disruptive cyber threats facing organizations today. These attacks can cripple businesses by encrypting critical data and demanding hefty
